




Key Croc from Hak5 is a keylogger equipped with pentest tools, remote access and payloads that trigger multi-vector attacks when entering selected keywords. It is the ultimate key-logging pentest implant.
More than just uploading and streaming keystrokes online, it takes advantage of the target through the payload that is triggered when you enter the keywords that interest you.
By emulating trusted devices such as serial, storage, HID and Ethernet, it opens up a number of attack vectors - from key injection to network hijacking.
Imagine getting credentials and systematically using them to extract data. Or roam anywhere, live in a Cloud C2 web browser.
It's also easy. The hidden button turns it into a flash drive, where changing the settings is just editing the text file. And with the root shell, your favorite pentest tools like nmap, responder, impacket and metasploit are ready.
KEY GAME CHANGER
The next generation of keylogging comes from the pioneers of Keystroke Injection - with an active payload of the attack.
Triggers a payload when writing a target matches a pattern - from a simple keyword to an advanced regular expression - even if the target makes a typo and presses backspace.
Save the number of keystrokes entered before or after the payload match. Then use these keyboard shortcuts in the Cloud C2 notification or actively against the target in the advanced payload.
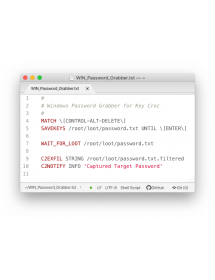
Imagine capturing keys pressed after a lock shortcut, such as [CTRL-ALT-DELETE] or [CTRL-CMD-Q], and then using the captured credentials to automatically start a silent filter.
MULTIVECTOR ATTACKS
Simulate a number of trusted USB devices at the same time. Navigate and inject keystrokes using HID attack mode. Gain network access to the target using Ethernet attack mode. Present Key Croc as a flash drive with Storage attack mode. Even emulate a serial device for some cunning attacks using serial attack mode.
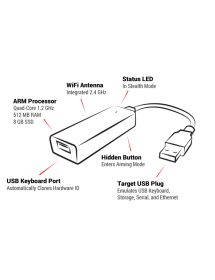
The full-featured Linux box has a root shell ready. And with its quad-core 1.2 GHz ARM CPU and desktop SSD, your favorite tools - from Nmap and Responder to Impacket and Metasploit - are just a few commands away.
CLOUD C2 READY
Play online from anywhere with the free, self-hosted Cloud C2 service, and watch real-time keystrokes. Or use your own live keystrokes directly from your web browser, get rid of loot, manage payloads, and even get a root shell for advanced attacks.
GET MORE ABOUT CLOUD C2
Easy configuration
Key Croc is already set to record keystrokes after unpacking. Just plug it in and you can go. It even automatically clones the keyboard hardware ID.
Then, to get the loot, simply press the hidden activation button. It will become a flash drive that allows you to copy logs by dragging and dropping.
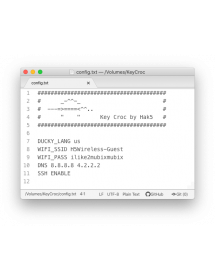
Activating useful data and configuring settings such as WiFi and SSH is as easy as editing a text file.
KEY FEATURES OF CROC
Connect and play
No configuration is required. After unpacking, keystrokes are recorded in the loot folder.
Cloud C² enabled
Remotely manage payloads, stream and enter keystrokes, extract loot, and even get a terminal directly from your web browser.
Detection leak
Don't be suspicious. Automatically clones the hardware identifiers of the connected keyboard.
Easy configuration
Pressing the hidden button changes it to a flash drive, so setting options and data is just editing a text file.
RGB LED status
It goes out when recording keys for a covert operation, but is incredibly useful when writing another payload.
Key injection
Introducing Ducky Script 2.0 - a de facto enhancement to the Keystroke Injection attack promoted by Hak5.
Network abduction
Gain direct network access to the target, bypass IDS and perimeter firewalls by emulating USB Ethernet.
Powerful hardware
Thanks to the quad-core 1.2 GHz ARM CPU and 8 GB SSD desktop computer, this is one impressive pentest implant.
Linux Base
Gain root access to the Debian base from a dedicated serial console or SSH to find pre-installed known Pentest tools.
WiFi enabled
With integrated 2.4 GHz antenna for great wireless performance.
No customer reviews for the moment.